heii folks
today i wanna talk about an bit i encountered during my regular work. the topic is the kinda niche and this is probably the cause that i have not found any information so far. the option i am talking about is the “requireNgcMfaForSecurityInfo” or if formated properly “require ngcmfa for security info” which is part of a API post request on the url https://mysignins.microsoft.com/api/session/authorize.
but let’s start at the beginning. during my work i encountered a strange behavior i wasn’t able to fully understand. when i logged in into the microsoft portal and later moved onto the Security info page (http://aka.ms/mfasetup) i got an mfa prompt. but i already was logged in and other application every other application accepted the current issued token which had the mfa claim in its amr field.
so i started some tests with my good old test account adam smasher.
First i tried to replicated the additional mfa prompt. i started with connecting to myaccount.microsoft.com while having an eye on the network tab in my browser dev tools and logged in with adam. afterwards i checked the issued mfa claims. follwing is a screenshot of parts of the jwt token decrypted with jwt.ms.
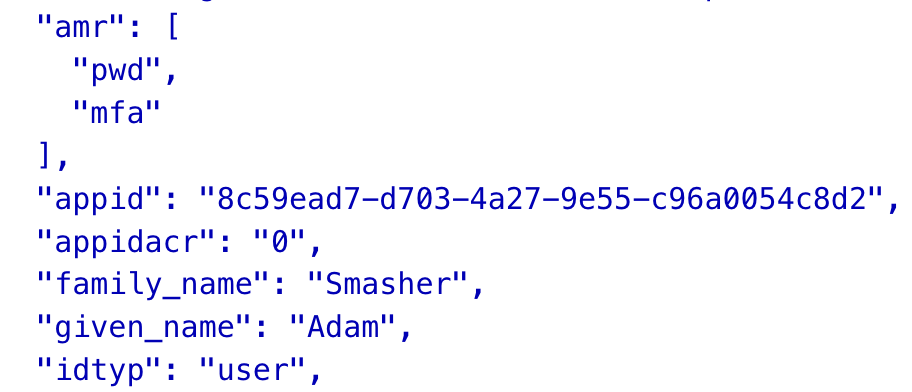
so i was able to verify that there was indeed already a mfa claim in my token proofing that i successfully did mfa.
but after i moved over to the security info page i got redirected to the login page and prompted to perform mfa again. this was the moment i checked the requests in the network tab again and found the following request.
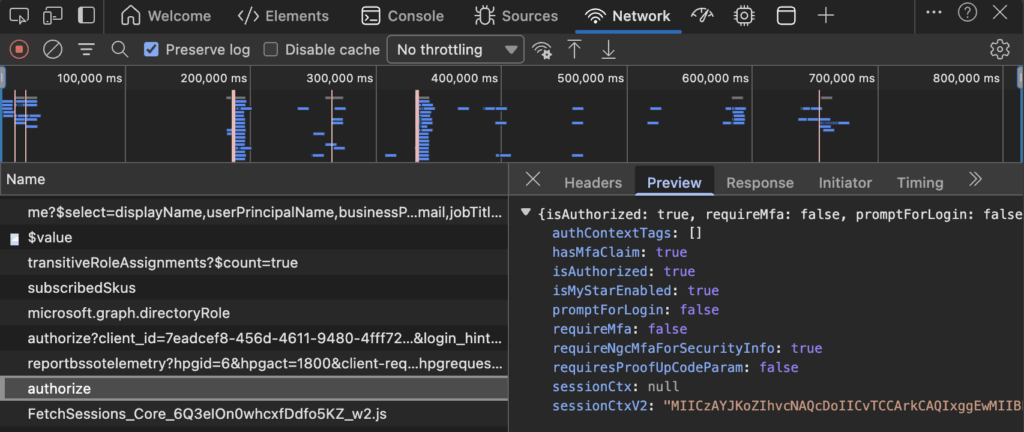
here i saw that i already satisfied mfa (hasMfaClaim: true) but in the bottom i saw that small key which caught my attention.
requireNgcMfaForSecurityInfo: true
as the portal asked me to do mfa so i did it and after the login i checked what claims i got into my token.
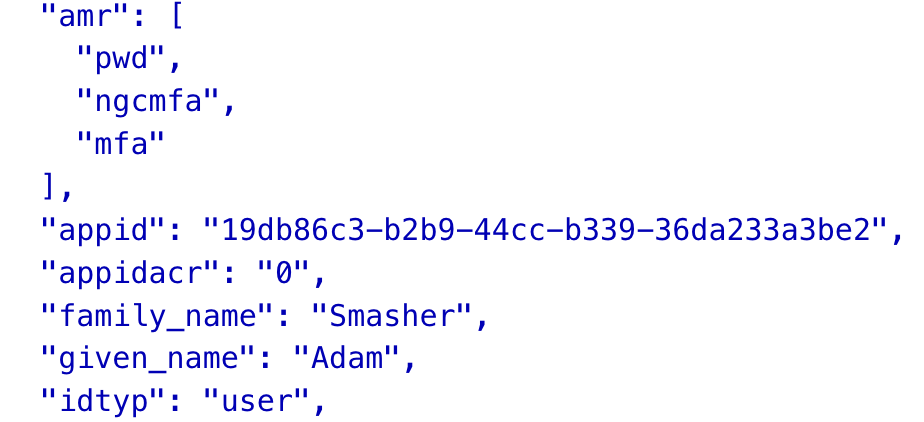
and there it is. the new ngcmfa claim within the amr section of my jwt token. with this i was able to open and close the security info page without any problems.
so if you ever encounter new/unexpected login prompts, try it yourself and check out what your browser tells you to understand how the system (might) work.
sources:
bonus: here is a copy of microsoft’s supported claims
| Value | Description |
| pwd | Password authentication, either a user’s Microsoft password or a client secret of an application. |
| rsa | Authentication was based on the proof of an RSA key, for example with the Microsoft Authenticator app. This value also indicates the use of a self-signed JWT with a service owned X509 certificate in authentication. |
| otp | One-time passcode using an email or a text message. |
| fed | Indicates the use of a federated authentication assertion (such as JWT or SAML). |
| wia | Windows Integrated Authentication |
| mfa | Indicates the use of Multifactor authentication. Includes the other authentication methods when this claim is present. |
| ngcmfa | Equivalent to mfa, used for provisioning of certain advanced credential types. |
| wiaormfa | The user used Windows or an MFA credential to authenticate. |
| none | Indicates no completed authentication. |
Funny side fact these amr values are not matching the rfc standard 8176.
here is the “official” list: https://www.iana.org/assignments/authentication-method-reference-values/authentication-method-reference-values.xhtml
bonus 2: wtf is ngcmfa?
definition 1 from the claim reference:
- Equivalent to
mfa, used for provisioning of certain advanced credential types.
source
definition 2: well the “best” definition i found is the following:
- Multiple factor authentication is required. User authentication with a certificate or other asymmetric key-based mechanism using a key that is present in the msDS-KeyCredentialLink attribute on the user object in Active Directory does not satisfy multiple factors, even if the key is protected by a smart card or requires a personal identification number (PIN) to unlock.
source
but since are pretty vague it’s probably time for some testing
cheers =^]
Leave a Reply